Anti-competitive practice from Microsoft. Microsoft is apparently pressuring some hardware vendors to lock their BIOS to prevent installation of 3rd party OSes including Linux. Someone bought a Yoga 900 ISK2 and found that they can’t install Linux on it.
Just when you thought Microsoft is turning good – from all the open-source and Windows Subsystem for Linux efforts.
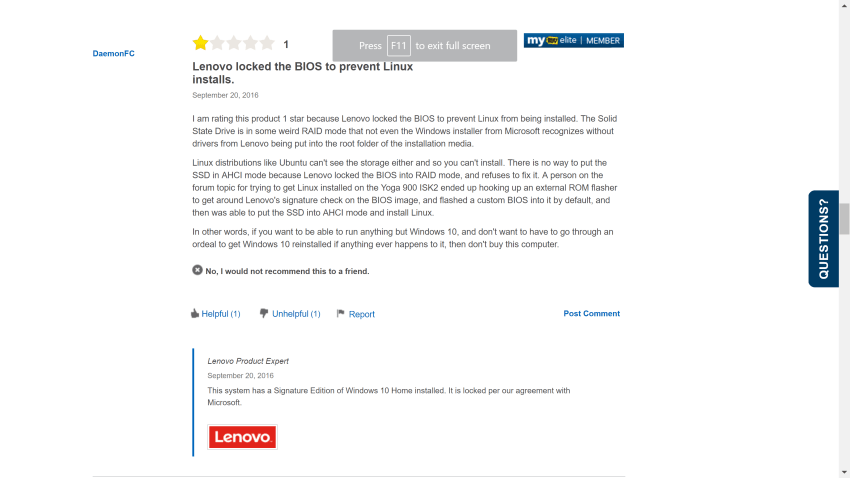
For you: If you see the “Windows 10 Signature Edition” badge on a laptop, DON’T BUY IT! You may not be able to install Linux (or any OS) on it, and there’s nothing you can do to the machine to change this currently.
Source: Beware: Windows 10 Signature Edition Blocks Installing Linux – FossBoss
Update (2016-09-22): Someone claims that the issue is overblown and that Ms isn’t forcing manufacturers to lock their BIOS. It’s Lenovo that is mishandling the whole thing.
Update (2016-09-22): Lenovo denies blocking installation of alternate OSes. Well they didn’t exactly block it. They just didn’t make it possible. If Lenovo wants to keep its customers happy it should release a BIOS patch that do exactly that.