Some people are alarmed when they read headlines like these. They may be wondering why Apple’s devices seem to be plagued by so many “security issues.” In fact, if you compare the number of CVEs (which, in layman’s terms, are security bugs) for Apple iOS versus Android, you will find that Android fares much worse in this aspect.
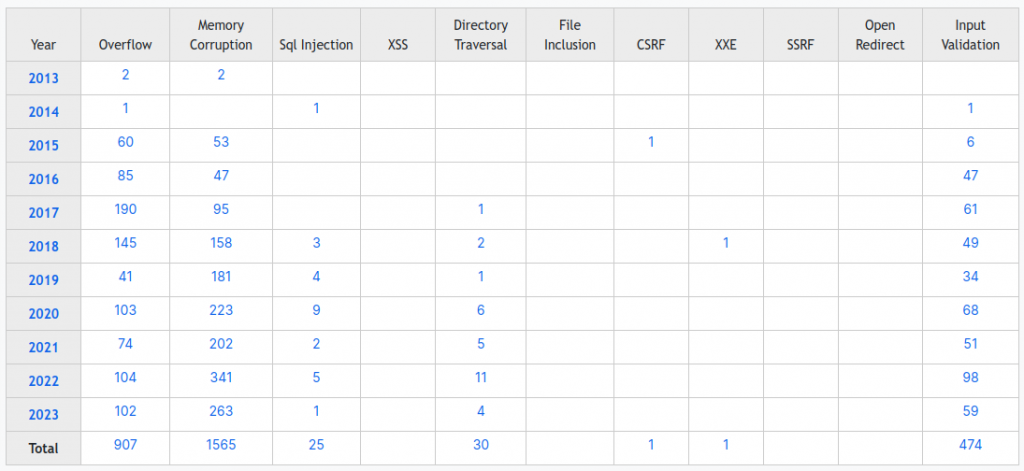
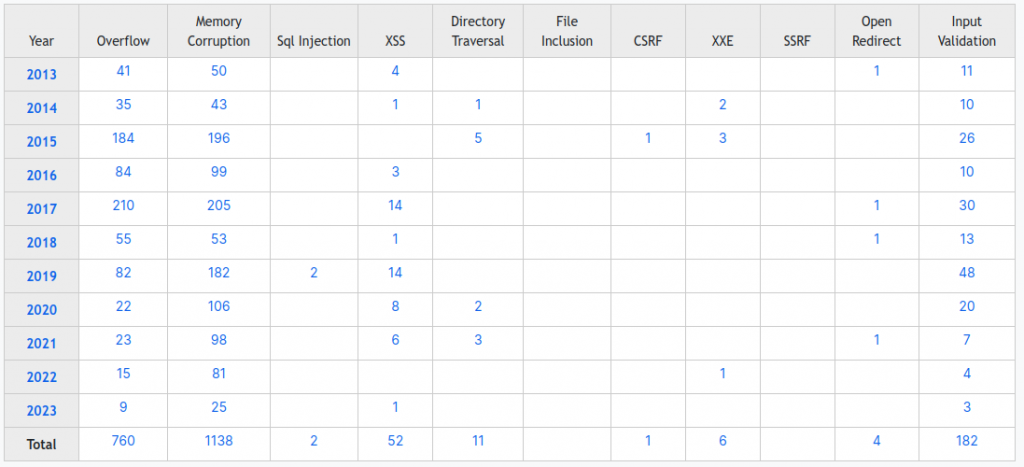
Android has 429 vulnerabilities reported for 2023 as of today, compared to 38 for Apple iOS – more than 10 times as much.
The reality is that all complex software is prone to bugs, and these bugs may or may not be exploitable. Further complicating the issue is that software is not a monolith; rather, it’s composed of numerous parts that are constantly changing due to upgrades, bug fixes, and other developments.
I’ve often said that maintaining running software is like paying a tax, even if “the specs are frozen” and “nothing is changed.” The fact is, things are constantly changing in the software world. New vulnerabilities are discovered in code or libraries, operating system updates roll out regularly, and the threat landscape evolves continuously.
So, why does it seem like Apple is frequently in the spotlight when it comes to security vulnerabilities? There are several reasons for this perception:
- Popularity and Visibility: Apple’s products, especially iPhones and Macs, are immensely popular worldwide. With a large user base, any security issue that does arise tends to receive significant media attention.
- Intensive Scrutiny: Apple’s closed ecosystem and stringent control over its hardware and software mean that security researchers and hackers alike often target the company’s products. The more scrutiny a system undergoes, the more vulnerabilities are likely to be discovered.
- Responsiveness: Apple takes security seriously and is quick to release patches and updates to address vulnerabilities when they are discovered. While this is a proactive approach, it also means that security issues might come to light more frequently.
- Zero-Day Vulnerabilities: Some vulnerabilities are so new and unexploited that they are termed “zero-day vulnerabilities.” These are often discovered in various software systems, including Apple’s. However, Apple’s high-profile status means that these vulnerabilities gain significant attention.
- User Expectations: Users of Apple products often have high expectations when it comes to security. Any perceived lapse or vulnerability can generate headlines and discussions.
In reality, all major operating systems, including iOS, Android, Windows, and macOS, face security challenges. The key is how these companies respond to these challenges and their ability to provide timely security updates to protect their users.
To stay safe in the digital age, it’s crucial to keep your devices and software up to date with the latest security patches. Additionally, practicing good cybersecurity habits, such as using strong, unique passwords, enabling two-factor authentication, and being cautious about the apps you download and the websites you visit, can go a long way in protecting your digital life. As technology continues to advance, so do the efforts of those seeking to exploit it. By staying informed and taking proactive security measures, we can all play a role in mitigating the risks associated with our ever-evolving digital landscape.