Today I received an email from a business associate whom I often corresponded with. Even though the email looks normal – it contains his full name and the usual email signature – something looks off.
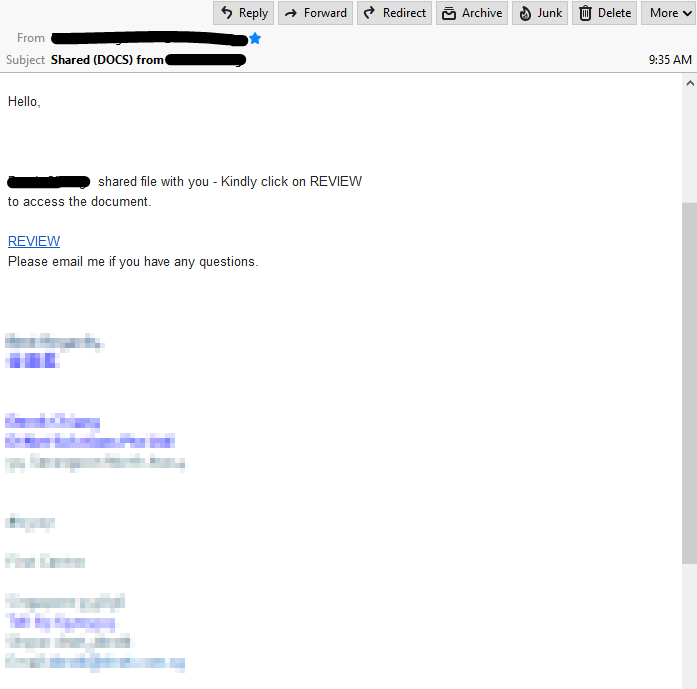
The email body is very terse and contains only a link – alarm bells start going off. The link points to a valid Google docs document.
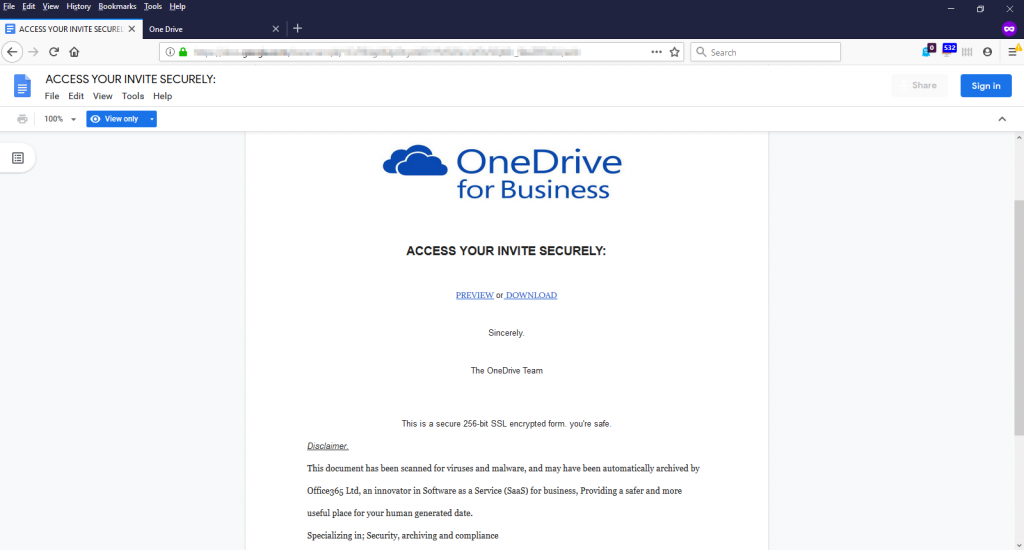
The document contains 2 links, both pointing to the same external site.
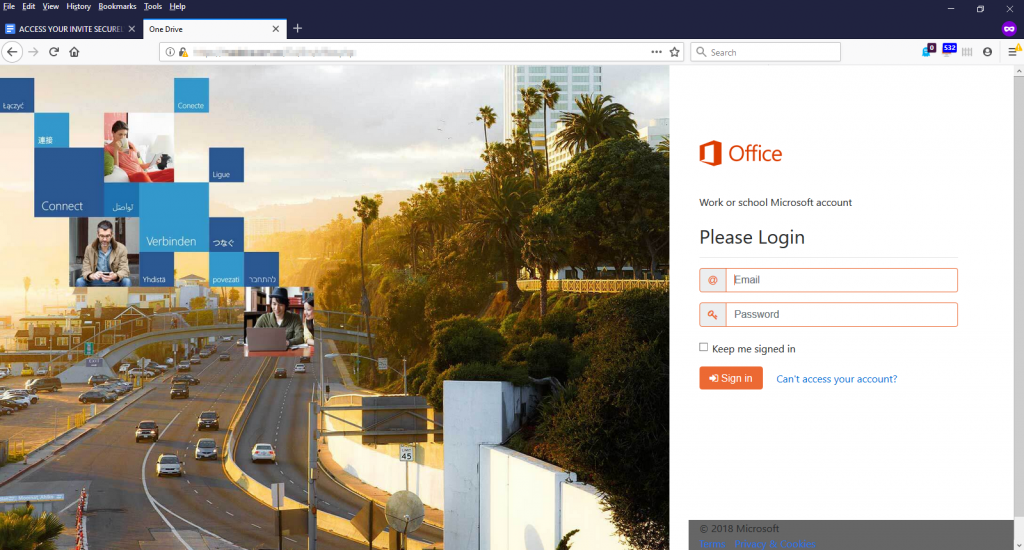
It is seemingly a login page for your Microsoft outlook account. But the domain is not associated with Microsoft. A classic phishing attack.
It so happens that the business associate is using Outlook for his email. After entering his credentials into the phishing site, the attacker must have used his credentials to send a copy of the phishing email to everyone in his contacts. Indeed that is the case, after I have confirmed with other associates. What makes this attack so successful is that 1) the email is from someone you have corresponded with 2) the first link opens a valid Google docs and some would have let their guard down at this point of time.
The latest report from FireEye states that 91% of cyber attacks comes from emails, and email-based attacks are getting increasingly more sophisticated. Some are also taking advantage of how email addresses are being shown on mobile devices.

As cyber threats continue to evolve, we must continue to educate users on the importance of maintaining vigilance and to be mindful of the limitations of current solutions to address the risks of phishing and other attacks.
Edit: I have submitted the phishing site to Google’s Report Phishing Page