IoT is increasingly becoming a dirty word for botnet.
Researchers have found ways to hijack a specific type of IoT device – the popular Philips Hue lamp – via ZigBee to do what they want, and make the attack spread wirelessly.
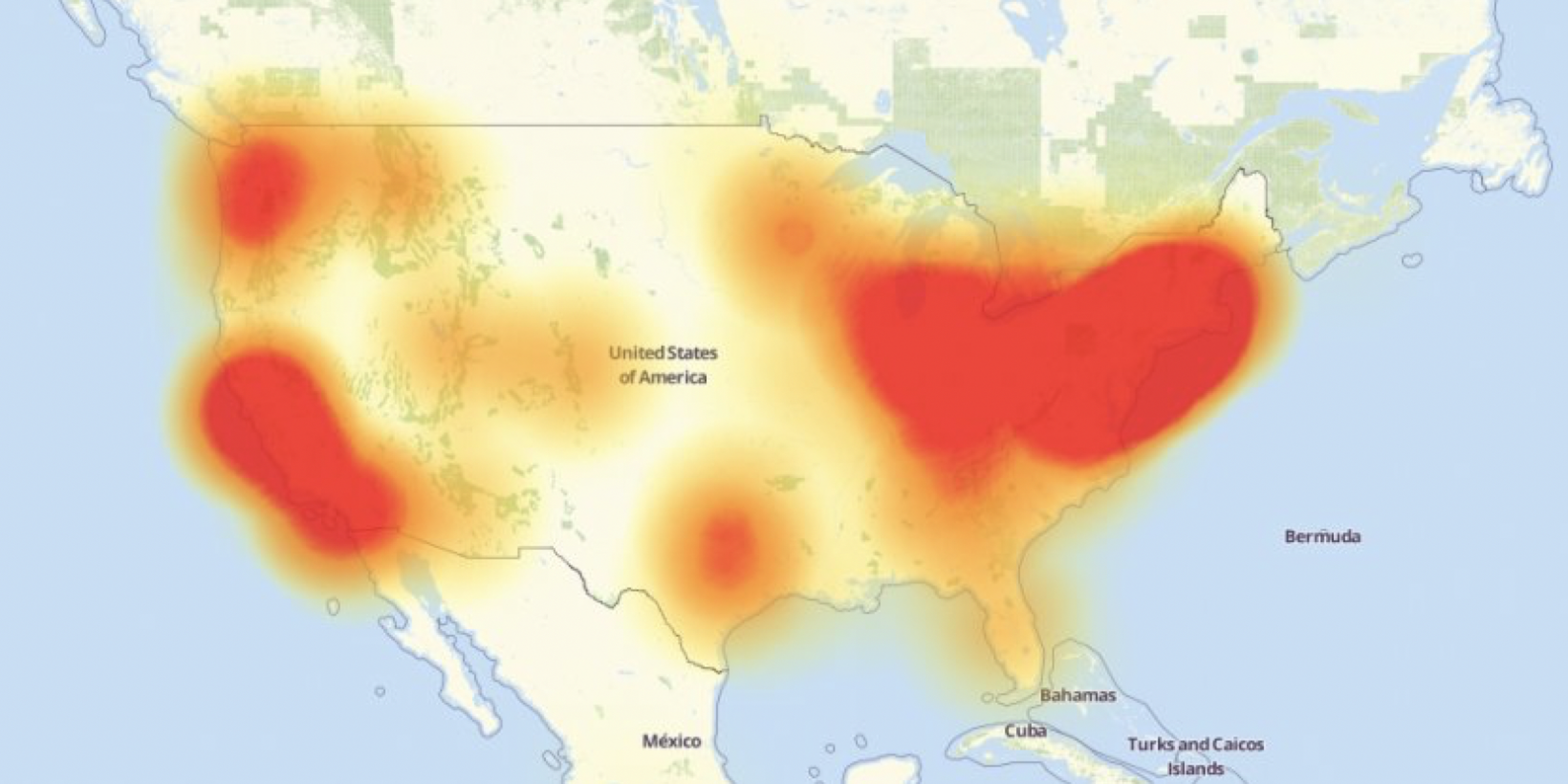
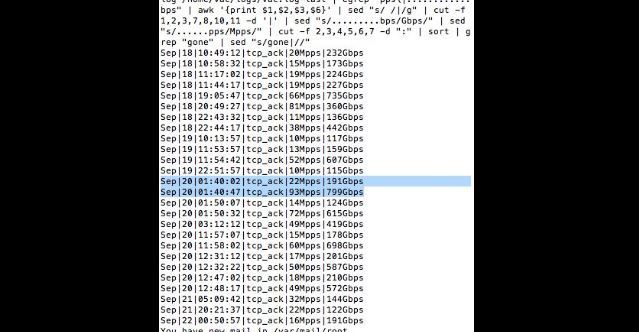
The worm spreads by jumping directly from one lamp to its neighbors, using only their built-in ZigBee wireless connectivity and their physical proximity. The attack can start by plugging in a single infected bulb anywhere in the city, and then catastrophically spread everywhere within minutes, enabling the attacker to turn all the city lights on or off, permanently brick them, or exploit them in a massive DDOS attack.