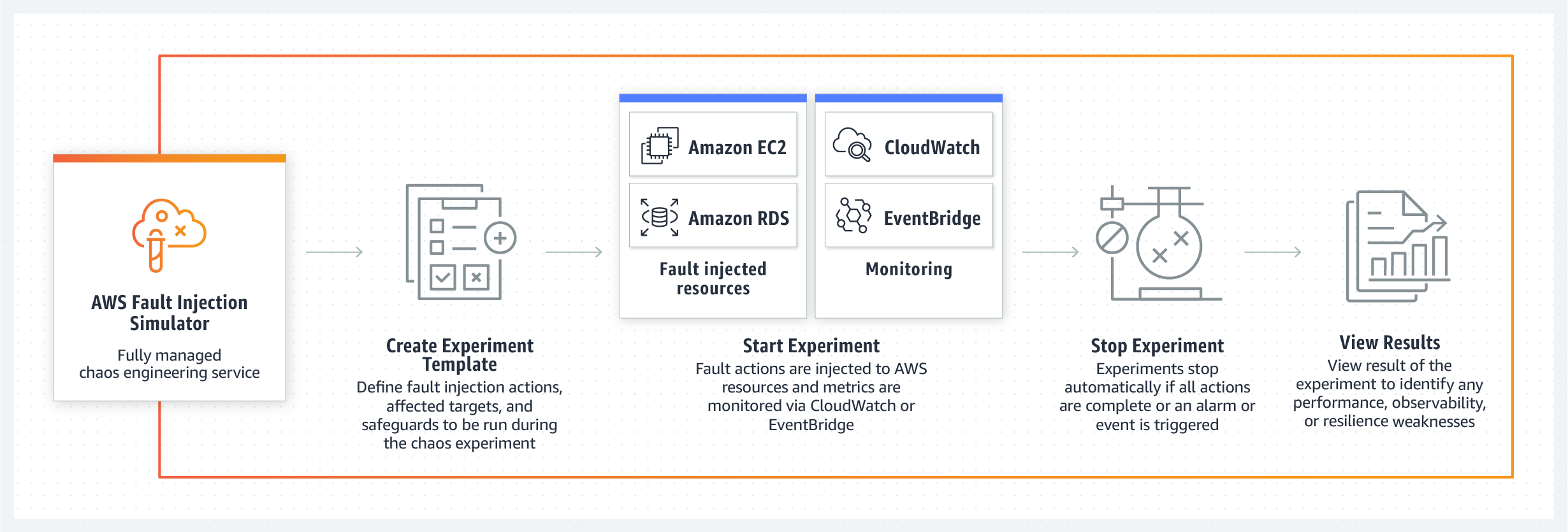
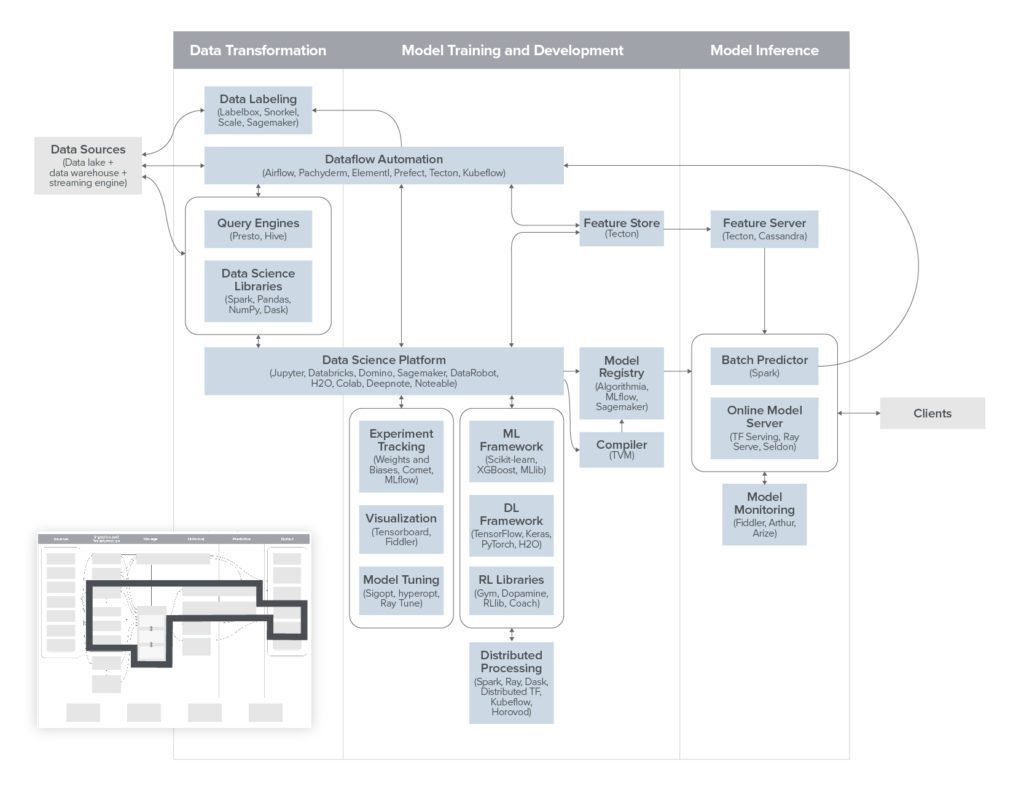
We are all familiar with spearphishing attacks against high value targets. But this is bold. A group of hackers are apparently targetting cyber security researchers, whose main job is to study them (the hackers) and their works. It’s like the thief stealing from the police. And the thief succeeded – in some cases.
Depending on how widespread the compromises were, it could potentially taint some research and defensive strategies that threat intelligence firms share with businesses and other organizations.
Source: Google discloses spearphishing targeting security researchers | SC Media