After years of procrastination, I finally did it. I am now using Linux not just on the server side, but as my primary OS, and I can’t be happier.
I have been a Linux user for most of my professional life, but my usage has been limited to the server side of things. Like most people, my working OS has been Windows from day one. There have been attempts to integrated the *nix way of doing things over the years: cygwin, git bash, WSL, running Linux in a VM under Windows. However, the user experience is clunky and there are always issues to work around.
It happens that the time has come to replace my primary working machine – currently a 5 year old notebook running Windows 10. I am a long time fan of the Intel NUC and thought it’s a good opportunity to kill 2 birds with one stone – setup a Linux desktop distro on the Intel NUC to try out the experience.
Choices
I managed to buy a 2nd hand Intel NUC (NUC8i3BEH), complete with 500GB SSD and 8GB RAM. It is not high-end or even mid-end by today’s standards, but I figured it should be good enough for testing.
The immediate problem is deciding which Linux desktop distro to install. And there are a lot of options out there. Since I’m familiar with Ubuntu I decided to limit my options to Ubuntu-based ones. I’m not a fan of the default Ubuntu experience with Unity. After much evaluation I decided on Linux Mint, as it is Windows-like, has LTS support, and does not use snap.
How
Downloading and install Linux Mint is straightforward. I chose the Cinnamon edition, as I wanted the default and up-to-date experience with Mint. On hindsight, I might have done better with Xfce, as it is uses less resources. More importantly, I discovered later that Cinnamon does not have the ability to restore applications (session restoration) after reboot, which Xfce does. It is not a showstopper, but would be a nice to have.
The default appearance and behaviour of Linux Mint is familiar enough that most Windows users would have no problem using it. However, I personally dislike the Mint start icon, and wanted to have a more Windows-like experience (the irony). Here’s what I did:
- Change the start button
- Change the trashbin icon
- Configure a more Explorer look-and-feel
- Change application icons (Thunderbird, Firefox)
- Change padding around icons in the taskbar
- Change shortcut for screen lock, workspace switch
Here is the initial result:
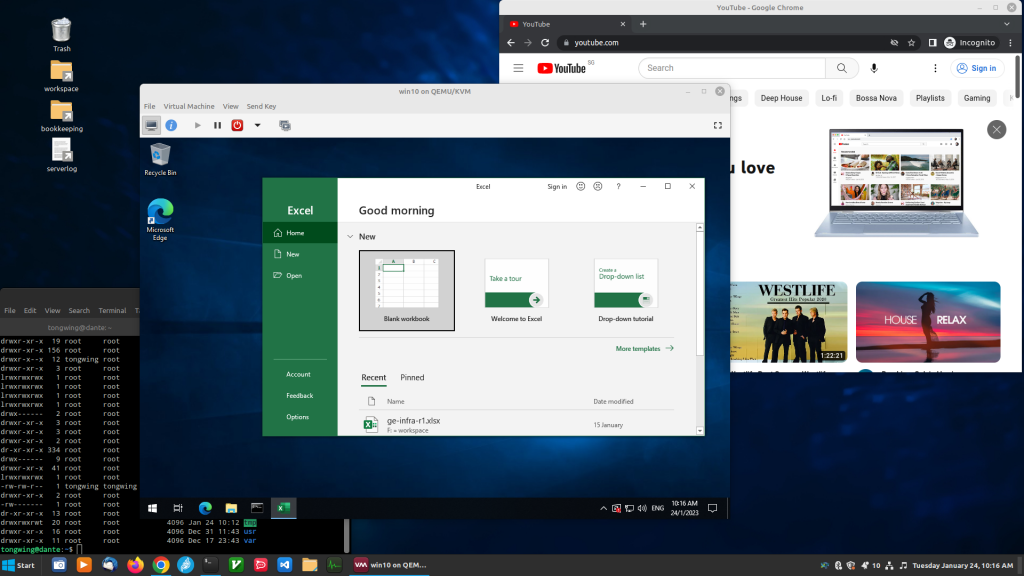
First Impressions
I am really surprised that everything feels so snappy. And this is on a low-end i3 processor from 5 generations ago. Going from cold boot to login screen takes 4 seconds. Booting a freshly installed Windows 10 in QEMU takes about 10 seconds. Firefox, Thunderbird, VS code all feels like they have been given a new lease of life. CPU and memory usage is low, compared to Windows 10 with the same number of applications opened. Bluetooth setup took a bit of getting used to, but after it is done everything just works.
Linux Mint comes batteries included, so as to speak. Some may not like it as it does have quite a number of applications that you may not use. But there are surprises like hypnotix which allows me to watch Bloomberg, CNN, CNBC for free, among others. It also comes installed with LibreOffice, which some may not like. Fortunately uninstalling software in Linux is normally a breeze. Mint comes with Software Manager, which makes finding, installing and uninstalling software very easy.
Other Setup
As with any new OS, there are lots of tinkering after the initial setup. Some other things I set up include:
- Flatseal – extremely useful to manage flatpak permissions.
- zram – extends swap with compressed RAM. Honestly I haven’t seen real benefits, but that’s probably due to the low memory usage at the moment.
- Samba – QEMU comes with Samba, so it’s just a matter of configuring it to share my folders with other Windows clients.
- Tailscale – Tailscale provides a way for all my devices to behave as though they are on the same network, even when they are not (eg. when I bring my notebook to office). It also works for phones. Read my other review.
- Remmina – Remmina is a remote viewer client that supports RDP and VNC and it works better than the default Remote Viewer client in Linux Mint.
- Barrier – virtual mouse/keyboard that works across Windows and Linux desktop.
- Syncthing – to synchronize files across multiple clients, for situations where the device might be used in an offline environment.
- PlayOnLinux – provides a persistent environment to run Windows applications in Linux via Wine.
- x11vnc – Linux doesn’t come with Remote Desktop built-in. One popular option is to use one of the VNC servers. x11vnc is a non-commercial solution and is as simple as it gets.
- Many others like Firefox, Chrome, Thunderbird, git, vscode, vim-gtk etc.
The Good Side
After using Linux Mint daily for 2 weeks, I have fully embraced it and notice I am not using my Windows notebook that much. Some benefits I noted so far:
- Fantastic developer experience
- docker, symlink etc just works
- QEMU is amazingly fast, compared to VirtualBox
- no more second class citizen using things like git bash, WSL
- Gnome terminal replaces command prompt, git bash and PuTTy (no more PuTTy key conversion)
- Control
- no unexpected Windows update happening at the most inopportune time
- no funny search indexer or software reporter running in the background causing CPU spikes
- no disappearing disk space due to WinSxS
- no more rebooting multiple times after installing applications
- no more extra folders/files like System Information, $RECYCLE.BIN and Thumbs.db littered everywhere
- Customization
- almost anything can be customized to your liking. You might have to find the right docs though
- Clean install/uninstall
- you don’t think twice about installing software ‘cos you can always uninstall them cleanly afterwards
Gotchas
It is not all a bed of roses however. There are some gotcha moments too, some which are unexpected:
- Installing software can be confusing for beginners, ‘cos there are so many ways to do it. You can do it either via a package manager like flatpak, snap, apt/deb, or portable style like AppImage, or adhoc-ly via tarball, curl/bash or compiling from source. It can also be hard to figure out where the config files are (/etc, .local, .config, dconf, within flatpak, etc.)
- Flatpak packages do not have access to the host file system by default. So if you drag a file from the desktop to your Flatpak app it might not work. This is a common gotcha that will catch Flatpak newbies off guard. Thankfully, you can easily manage permissions using Flatseal.
- The size of software packages installed can vary wildly depending on packaging type. In one rather extreme example, for the same package, it can take either 1.1MB or 2.3GB(!). More than 2000x difference!
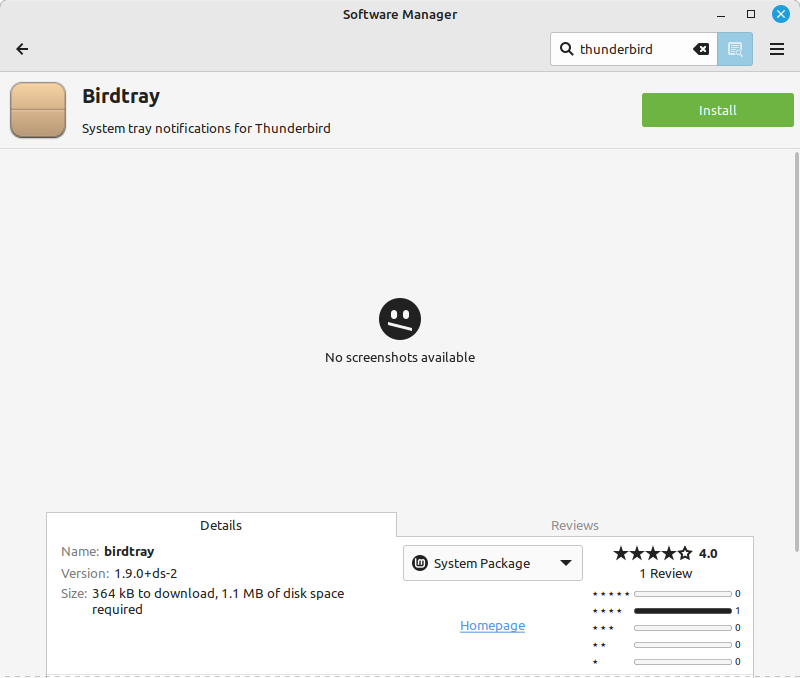
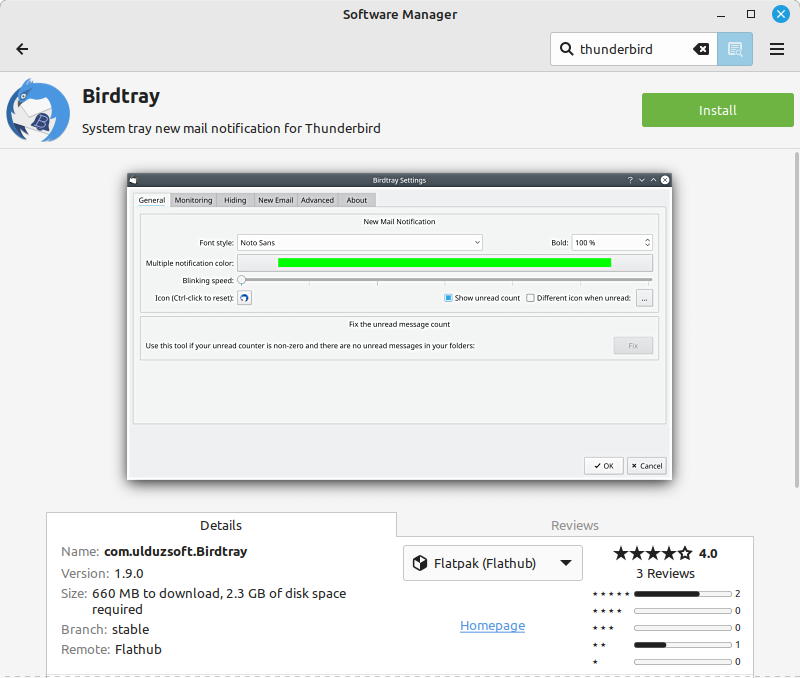
- Obviously the biggest drawback of a Linux desktop is the inability to run native Windows programs. Well, Wine does a pretty admirable job, but it cannot cover the huge surface area of the Windows API and ecosystem. Running stuff in a VM is sometimes not ideal. I end up falling back to my Windows notebook for the following software:
- Microsoft Office (yes I know you may be able to run Office 2016 32-bit using Wine, but I don’t really want to go that route)
- Hyper-V manager
- SketchUp
- 3DS Max
- iTunes
TeamsMicrosoft actually has a Linux version of Teams. Good job!
Remaining Issues
There are some unresolved problems at the time of writing:
- VPN gets disconnected after my NIC link goes down and up. I have yet to find a good way to restart VPN automatically in network manager.
- XMind does not open a document that is double-clicked in Files. It just launches the application without opening the document.
- There is an ever-so-slight initial delay when moving the mouse from rest. Not sure if it’s a bluetooth, driver, or window manager issue. Not a showstopper, but can be annoying.
- Systray integration in Linux is surprisingly weak. The official Thunderbird doesn’t have systray integration, which means you can’t tell when there’s a new mail or how many unread mails there are. There are unofficial solutions like BirdTray but it doesn’t seem to work with the latest Thunderbird versions.
Conclusion
Given the list of issues I’ll still take Linux over Windows any day. The amount of control – and peace of mind! – you get is irreplaceable. Not to mention good performance, low CPU/memory footprint, amazing developer experience, and stability you get (bye to BSOD). For those who are sitting on the fence, my advice is this: don’t wait! There might be a bit of learning curve, but it is well worth it.