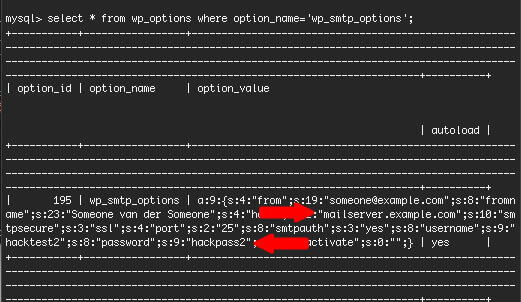
ImageMagick and its fork – GraphicsMagick – are widely used libraries by tons of applications for “displaying, converting, and editing raster image and vector image files”.
All existing releases of GraphicsMagick and ImageMagick support a file
open syntax where if the first character of the file specification is
a ‘|’, then the remainder of the filename is passed to the shell for
execution using the POSIX popen(3C) function.
via CVE Request: GraphicsMagick and ImageMagick popen() shell vulnerability via filename