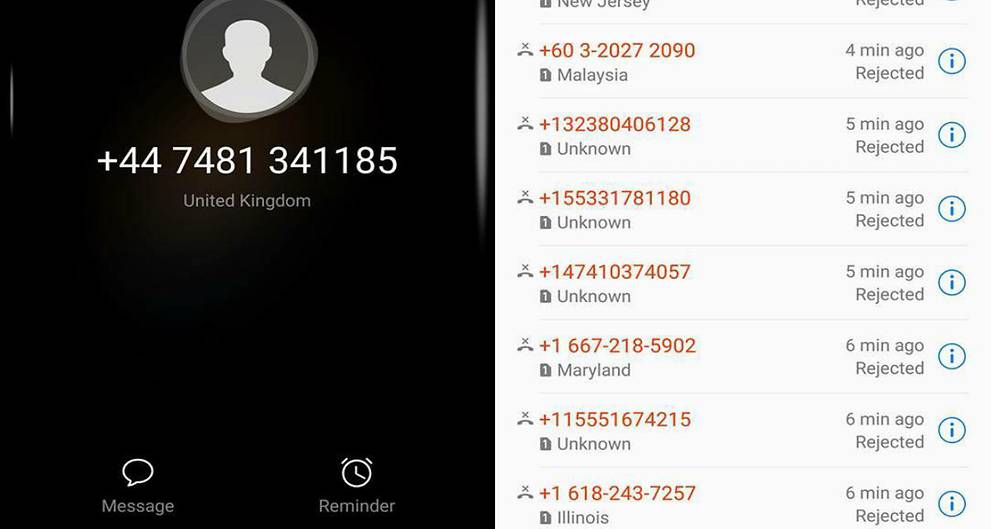
This is the classic DDoS attack, but with a twist. Instead of spamming servers through the Internet, someone is spamming phone lines through a phone botnet. Similar to DDoS, this makes it difficult for legitimate calls to go through.
Candidates for Malaysia’s 14th general election have claimed that their phones have been hacked and spammed with calls from overseas numbers.
Source: Malaysia general election candidates slam ‘dirty trick’ spam calls; Najib orders action