What is it?
The so-called unified QR code is finally out.
SGQR code is purportedly Singapore’s effort in “unifying” the fragmented e-payment market – what with DBS PayLah!, Singtel Dash, Grab Pay, LiquidPay, AliPay etc coming into the fray.
MAS says:
For consumers
Your current payment app probably works with SGQR already. All you need to do at the merchant checkout is:
• PICK and launch your preferred payment app
• SCAN the SGQR and check the merchant name
• PAY the correct amount
In other words, ideally a consumer can use his/her preferred payment app to make payment to a merchant through SGQR.
How well has it achieved its goals?
There are some upsides and some downsides. On the upside, consumer will only see one QR code per merchant. So it is less confusing compared to now where the payer have to carefully match the array of QR codes being shown to the right app.
On the downside, while the SGQR specification can enable multiple e-payment providers, merchants are unlikely to sign up with ALL of them (up to 27 payment schemes). So you can end up in a situation where you see a SGQR code but are unable to use your preferred payment app (say Grab Pay) to make payment. The payer have to look at the row of icons below the QR code to know which e-payment solution is accepted.
Technical Details
Very little technical information is publicly available about this SGQR code. After some research, I found on MAS website that it’s based on EMVCo QR code. EMVCo is made up of members from American Express, Discover, JCB, Mastercard, UnionPay, and Visa, and is the body that creates standards for secure payment.

Let’s try and see what the QR code contains. Fortunately the QR code in the article is clear enough to be decoded:
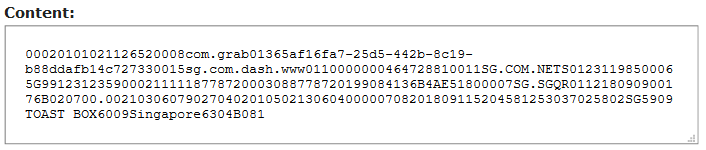
To parse the content of the QR code, one can refer to the EMVCo QR code specifications which is available on the EMVCo website.
After a bit of parsing,
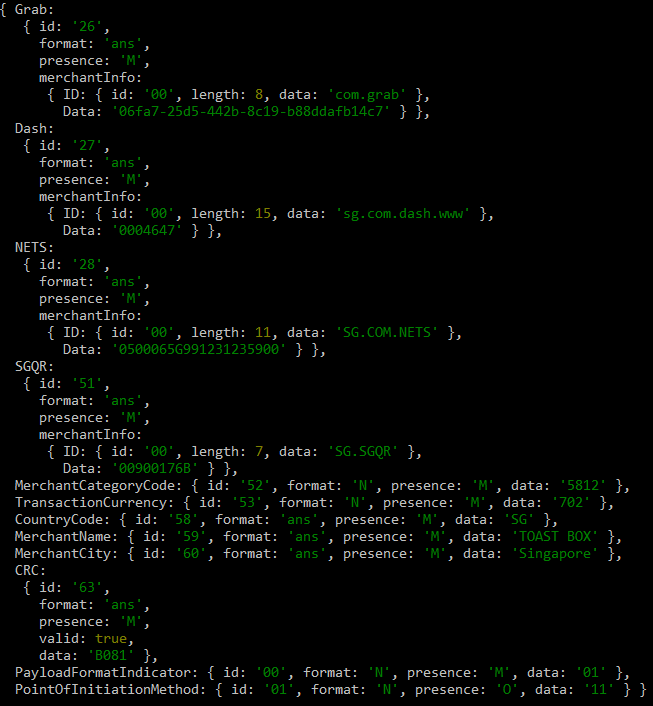
It’s clear that this QR code contains meta-data for only some payment providers.
Conclusion
We are still in the early days of SGQR. It remains to be seen how widely adopted businesses and consumers will take to this form of payment.
For now, the only thing it probably saves is real-estate for display QR codes.
Update (2018-09-21): Yeah! This article made it onto the front page of Hacker News! See the comments on HN here.