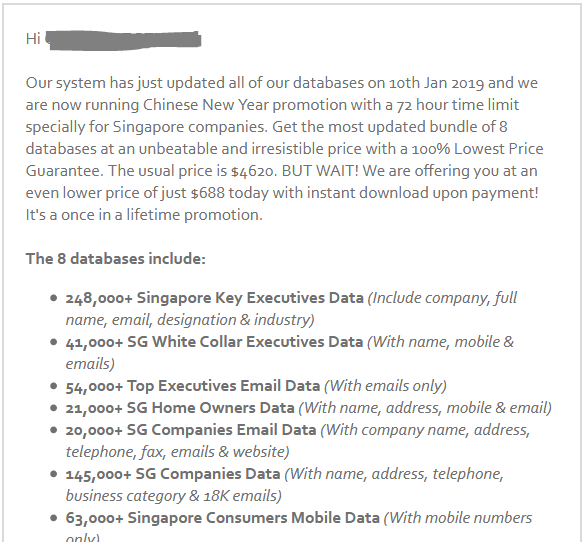
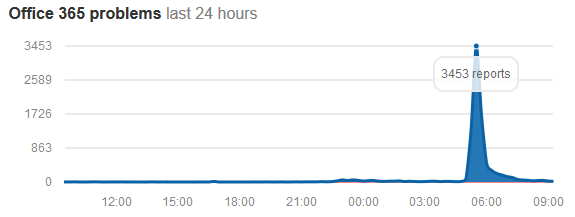
This is a serious one. A vulnerability exists on Android that will allow the phone to be hacked simply by viewing a malicious PNG image.
The most severe of these issues is a critical security vulnerability in Framework that could allow a remote attacker using a specially crafted PNG file to execute arbitrary code within the context of a privileged process. The severity assessment is based on the effect that exploiting the vulnerability would possibly have on an affected device, assuming the platform and service mitigations are turned off for development purposes or if successfully bypassed.
Source: Android Security Bulletin — February 2019 | Android Open Source Project