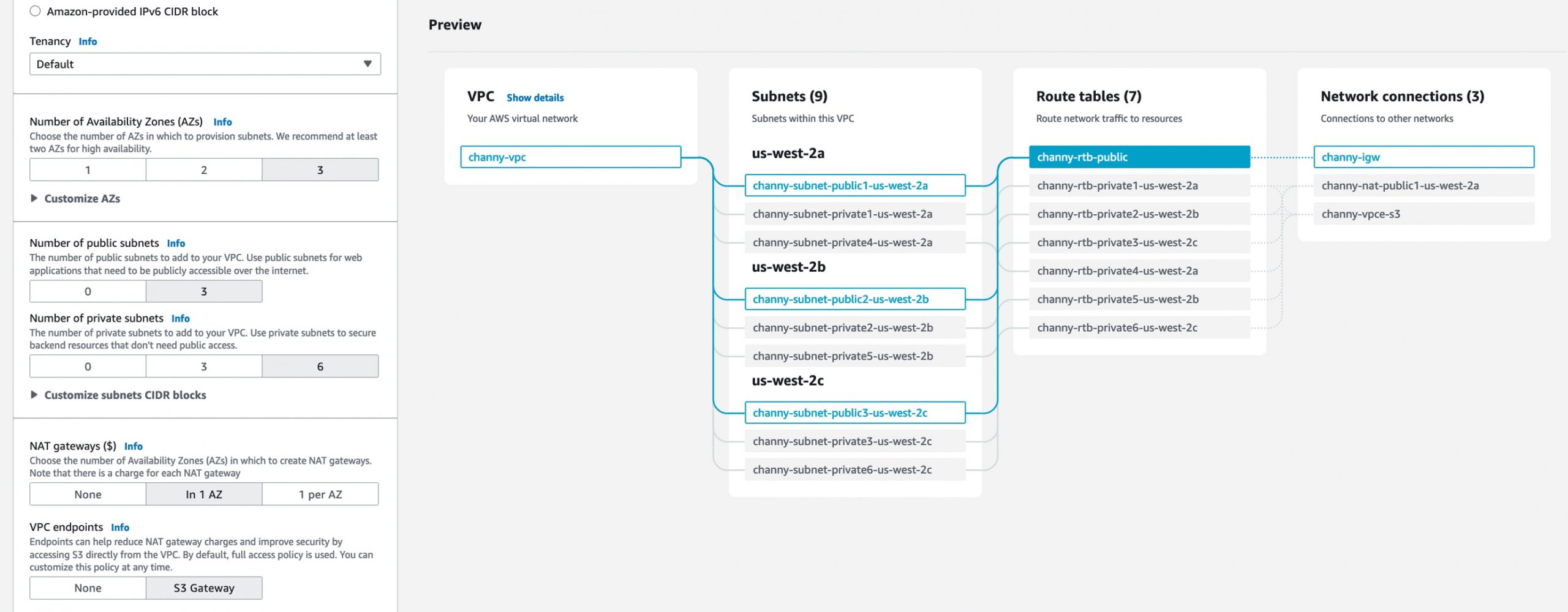
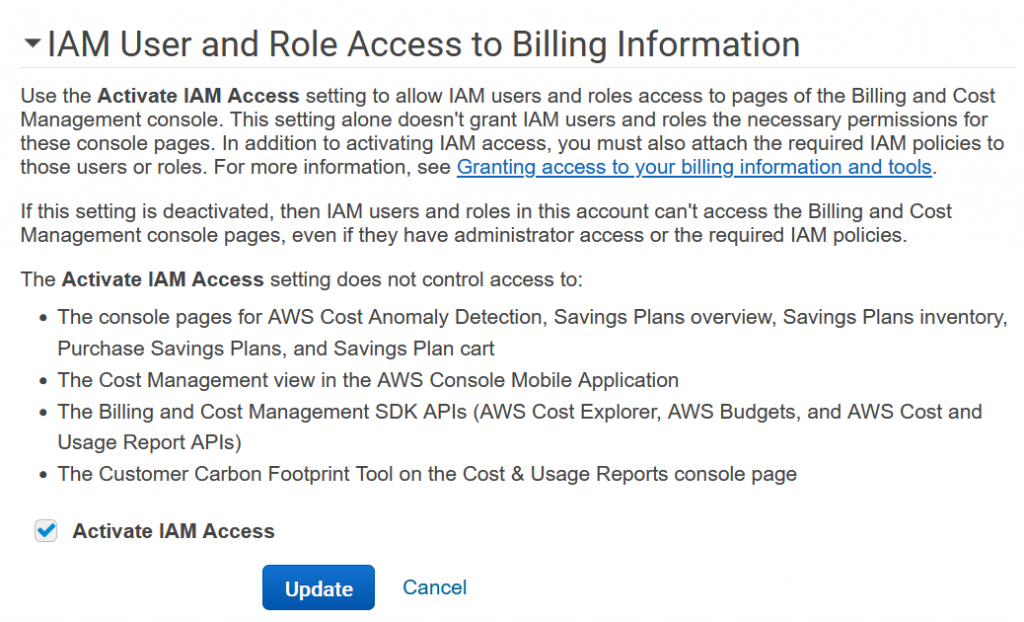
Finally. Amazon Web Services has released a new feature called Amazon Virtual Private Cloud (VPC) resource map, which simplifies the VPC creation experience in the AWS sonsole. This feature displays existing VPC resources and their routing visually on a single page, allowing users to quickly understand the architectural layout of the VPC.
The new VPC creation experience streamlines the process of creating and connecting VPC resources with just one click, even across multiple Availability Zones (AZs). The VPC resource map also allows users to quickly understand the architectural layout of the VPC, including the number of subnets, which subnets are associated with the public route table, and which route tables have routes to the NAT Gateway. Additionally, users can customize a Name tag per resource in the preview and easily change the default CIDR value and subnet mask. The Amazon VPC resource map is now available in all AWS Regions where Amazon VPC is available.