Disclaimer: The following analysis of what could have happened is pure speculation based on publicly available information.
On 8 Jan 2022, news broke that as many as 469 OCBC bank customers were affected by phishing scams, racking losses of up to S$8.5 million in total. This should be one of the biggest and most successful phishing attack of a Singapore bank in recent memory.
Based on details of the news report, it appears that the scam works mainly as a result of 2 factors:
1. Successful social engineering
2. Possible SMS hijacking
Fake bank SMS
According to reports, users who got scammed received SMS messages that appear to originate from the bank. Scammers prey on user’s tendency to trust messages that appear alongside previous legitimate SMSes. How scammers are able to do this is to make use of a feature of SMS sending known as Alphanumeric sender ID. Meaning, they can send an SMS with a chosen sender ID that the bank uses. In this case, they chose “OCBC” as the sender ID. When the user receives such a SMS, it will appear alongside existing SMSes from the same sender ID “OCBC”.
As a quick test, I sent myself a test message with sender ID set to “BOC SG” (what Bank of China Singapore uses) and this is what I see:
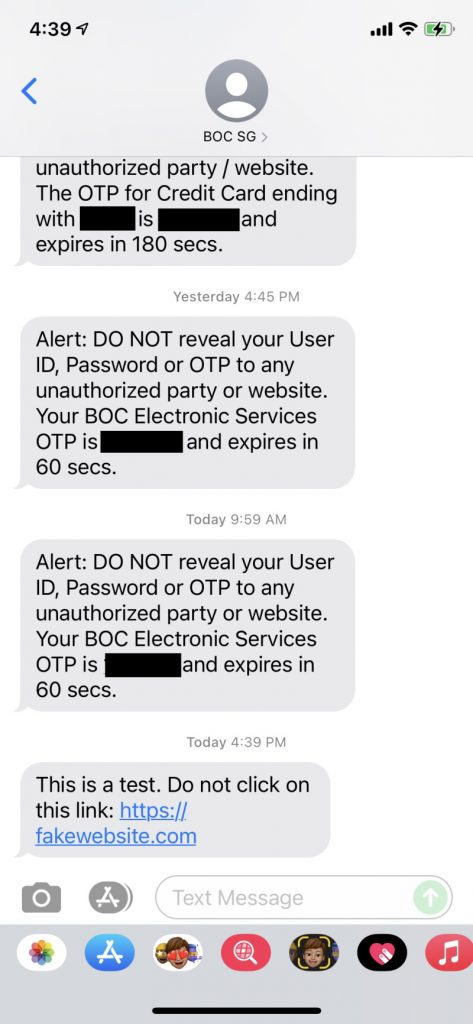
This is just to show how easy it is to fake a sender ID. Interestingly, I was unable to reproduce this using “OCBC” as the sender ID, probably because the service provider/ISP is filtering out such IDs.
If a user thinks that it is a legitimate message from the bank, they tend to let their guard down and click on the link that the “bank” has sent – especially if it’s worded as something urgent. In this case it directs to a phishing site that looks exactly like the bank’s login page. Once the user enters their login user/password, the scammer would have captured their login credentials.
SMS hijacking
Just having login credentials is insufficient to make the attack successful. Because most banks would require 2FA for full login and to perform other more important actions like money transfer. This is where the SMS hijacking comes in.
It has been known for quite some time that SMS is NOT a reliable form of 2FA. To understand why, we have to dig into how SMS is implemented. Those who are interested can find out more here. There are some sites – which I won’t link to – that offers to provide such hijacking service for as little as $16.
To cut the long story short, if an attacker knows your mobile phone number, they can intercept your SMS messages, without you knowing. Shocking. I know. But this is well known and has been repeatedly demonstrated in cybersecurity conferences and other public forums.
With both the login credentials and hijacked SMS messages carrying OTP messages, an attacker can in theory carry out transactions without the user being notified.
Actually that is not all, if the bank calls your mobile number – for example, to verify the transaction – that can be intercepted as well via the same mechanism.
Closing the gap
The attack worked in this case because Singapore allows for Alphanumeric sender ID without requiring pre-registration by the sending organization. There are now renewed calls to make pre-registration compulsory to use this feature.
Fixing SMS hijacking – if it’s indeed the mechanism being used – will take more effort and probably require all ISPs to put in place mitigation in their systems. The easier fix may be to deprecate SMS as a 2FA option and stick to other more secure options like authenticating through app or physical tokens.
There are also some questions as to why automatic fraud detection that banks usually have in place is not working in this case. I shall not speculate on this but wait for further information from the investigation.
Conclusion
OCBC customers are not the first to fall prey to scams and neither will they be the last. As we move more and more to the digital world we can expect cyber criminals to keep exploiting both technical loopholes as well as human weaknesses to achieve their objectives. User education remains important and so are improving processes and closing technology gaps.