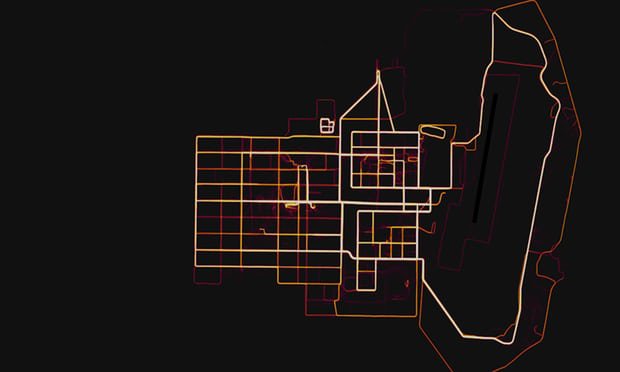
IOW, location data can be mined for valuable information. The proliferation of sensors in everyday devices and the rapid adoption of IoT has put the spotlight on the problem.
This was all sparked when reports surfaced earlier this year of a fitness-tracking company, Strava, publishing maps showing where users jog, bike and exercise. Since many of its users are members of the military, their jogging routes and other exercises showed exactly where the US has service members around the world, as well as showing their running routes.