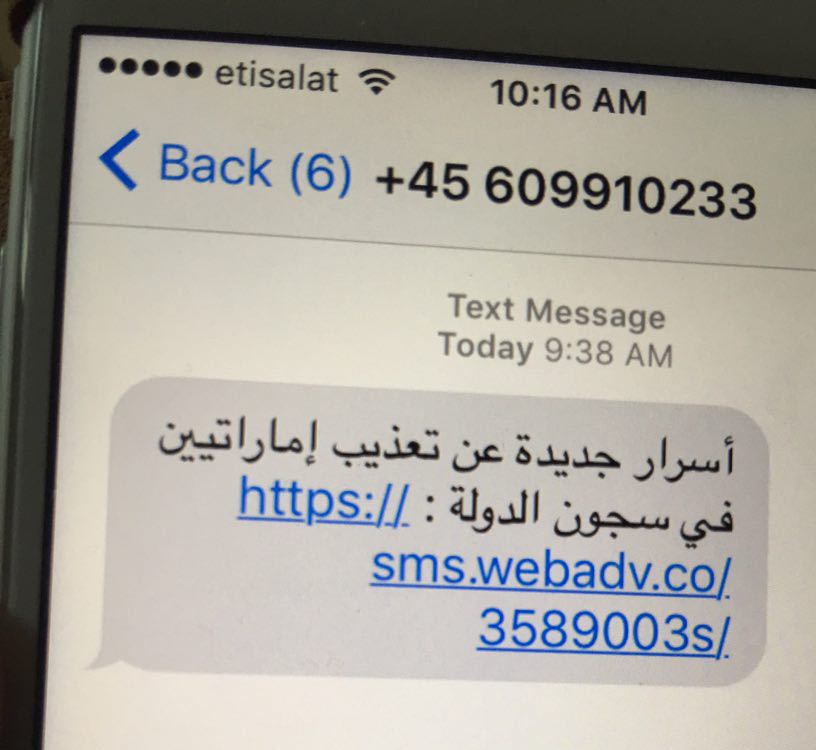
The dark side of the cybersecurity industry has surfaced once again – companies that provide cyberweapons to organizations with deep pockets. In this case, the cyberweapon is a chain of zero-day exploits that requires no more than clicking on a link from an SMS. Good thing the target is discerning enough not to click on it – which means a million dollars (or two, or three) is wasted.
This report describes how a government targeted an internationally recognized human rights defender, Ahmed Mansoor, with the Trident, a chain of zero-day exploits designed to infect his iPhone with sophisticated commercial spyware.