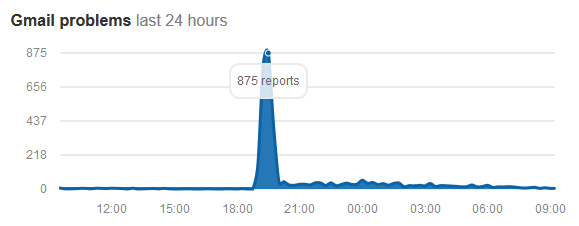
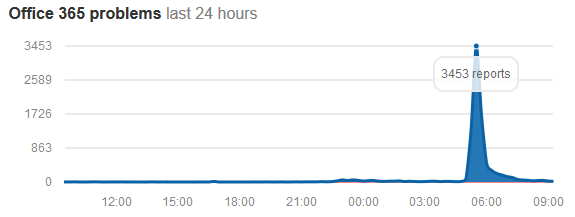
This is not a good day for cloud services. Gmail outage followed by Office 365 outage (unrelated).
Month: January 2019
This is a serious hijack of a toolchain used by developers.
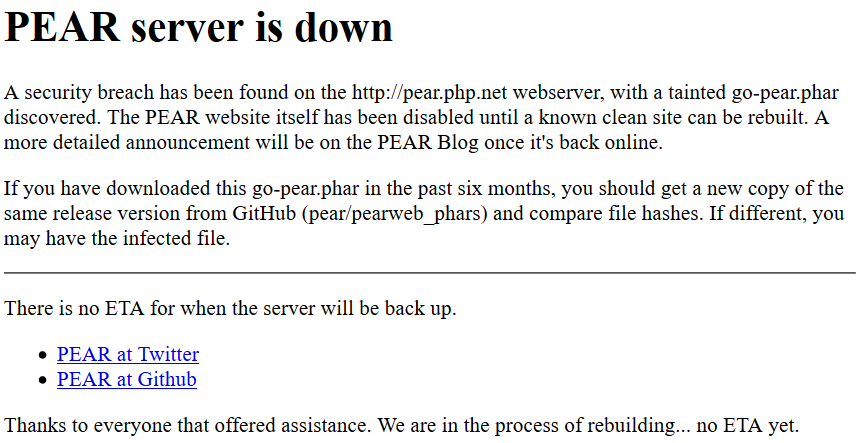
Pear.php.net shuts down after maintainers discover serious supply-chain attack.
Source: If you installed PEAR PHP in the last 6 months, you may be infected | Ars Technica
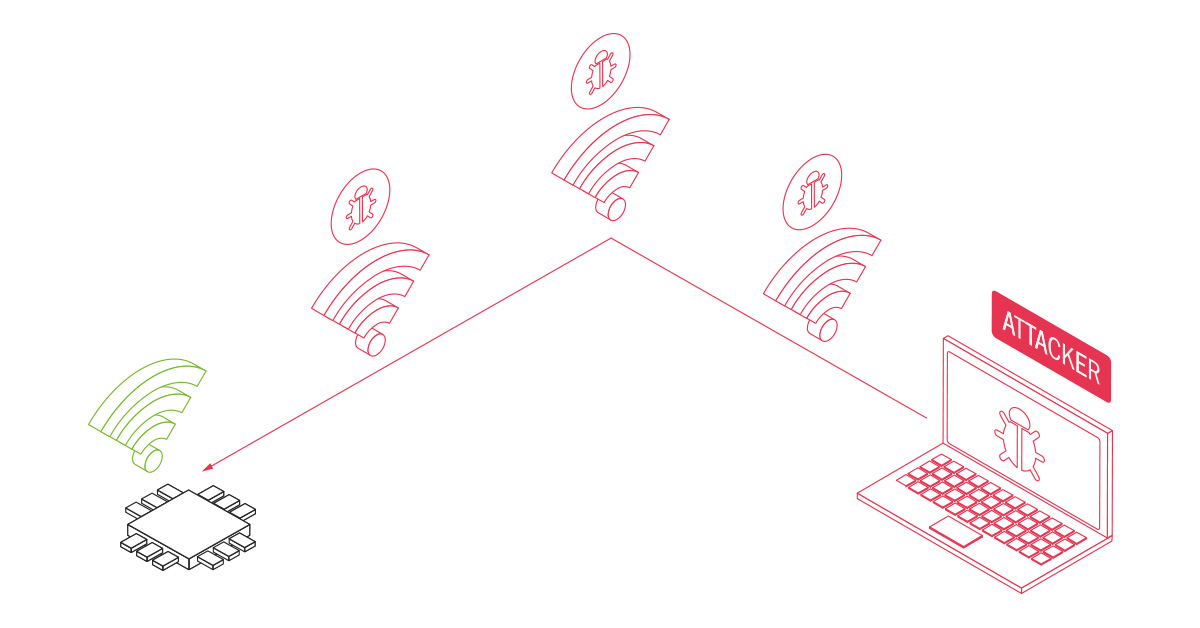
Marvell Wifi System-on-chip, which is used by Valve Steamlink, PS 4, Microsoft Surface and Samsung Chromebook is susceptible to remote compromise. Here’s the kicker: the device can be compromised just by the fact that it’s powered on. There is no need for the victim to visit any website or click on any links. That’s what makes this RCE (remote code execution) so dangerous and potent.
This vulnerability can be triggered without user interaction during the scanning for available networks. This procedure is launched every 5 minutes regardless of a device being connected to some Wi-Fi network or not. That’s why this bug is so cool and provides an opportunity to exploit devices literally with zero-click interaction at any state of wireless connection (even when a device isn’t connected to any network).
This is a case that will test the limits of exclusion in the brave new world of cybersecurity insurance. Basically, the insurance company is refusing to pay for cybersecurity related damages by citing an exclusion clause which states the malware was created as part of a cyber warfare.
What if courts and lawyers actually start believing the cyberwar narrative and acting as if any damage caused to Western companies is uninsurable war damage?
…
What will happen to the insurance of cyber risks if any attack could potentially be declared part of a war?
Source: Mondelez Lawsuit Shows the Dangers of Attributing Cyberattacks – Bloomberg
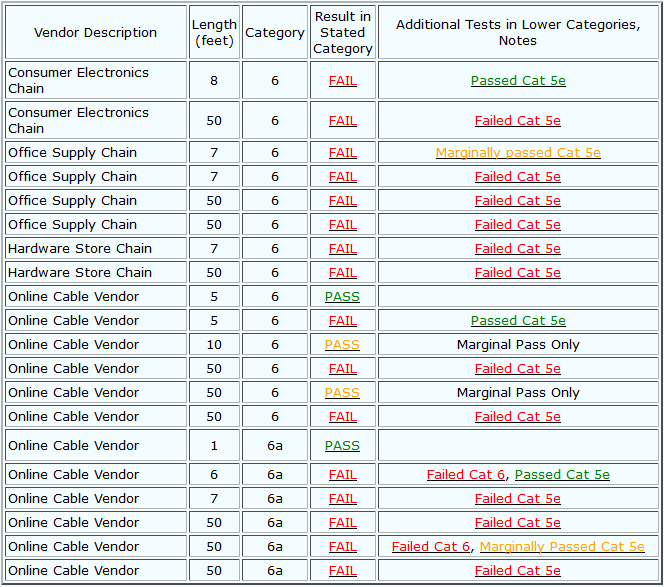
The state of Cat 6 cables sold in the market is appallingly bad.
Plainly enough, most of these cables aren’t designed to meet Cat 6 or 6a specifications, and they’re certainly not tested for compliance before leaving the plant.
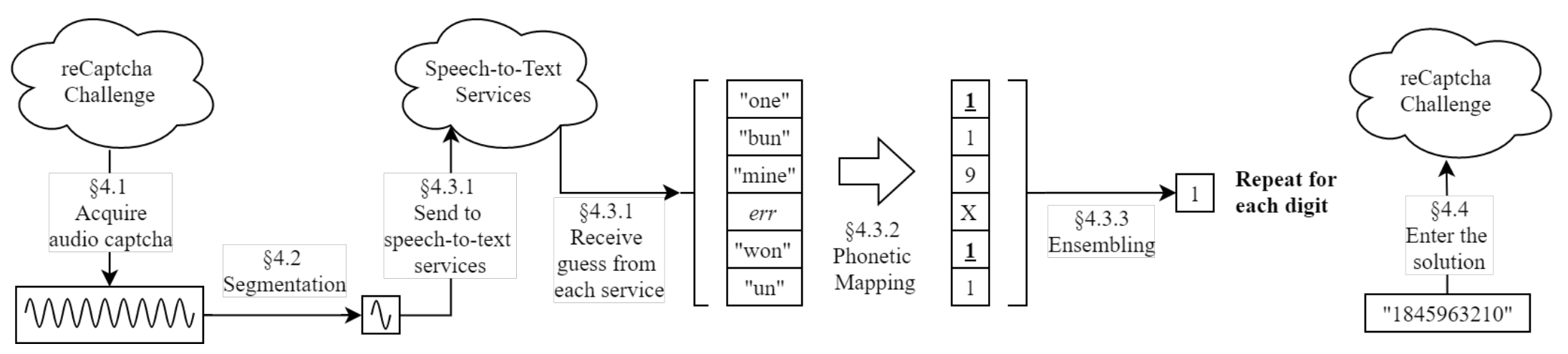
CAPTCHA is almost ubiquitous in today’s web applications and an extremely popular CAPTCHA implementation is Google’s, namely reCaptcha. reCaptcha provides an audio version for visually-impaired users. Researchers manage to make use of free speech-to-text services to defeat audio reCaptcha.
unCaptcha: Talk is cheap in defeating reCaptcha
Source: unCaptcha: A Low-Resource Defeat of reCaptcha’s Audio Challenge
“Why stop at 4?”
Nokia’s next flagship Android phone features five cameras, a 5.99-inch PureDisplay, more.
Source: Nokia’s Next Android Flagship Features Five Cameras – Thurrott.com