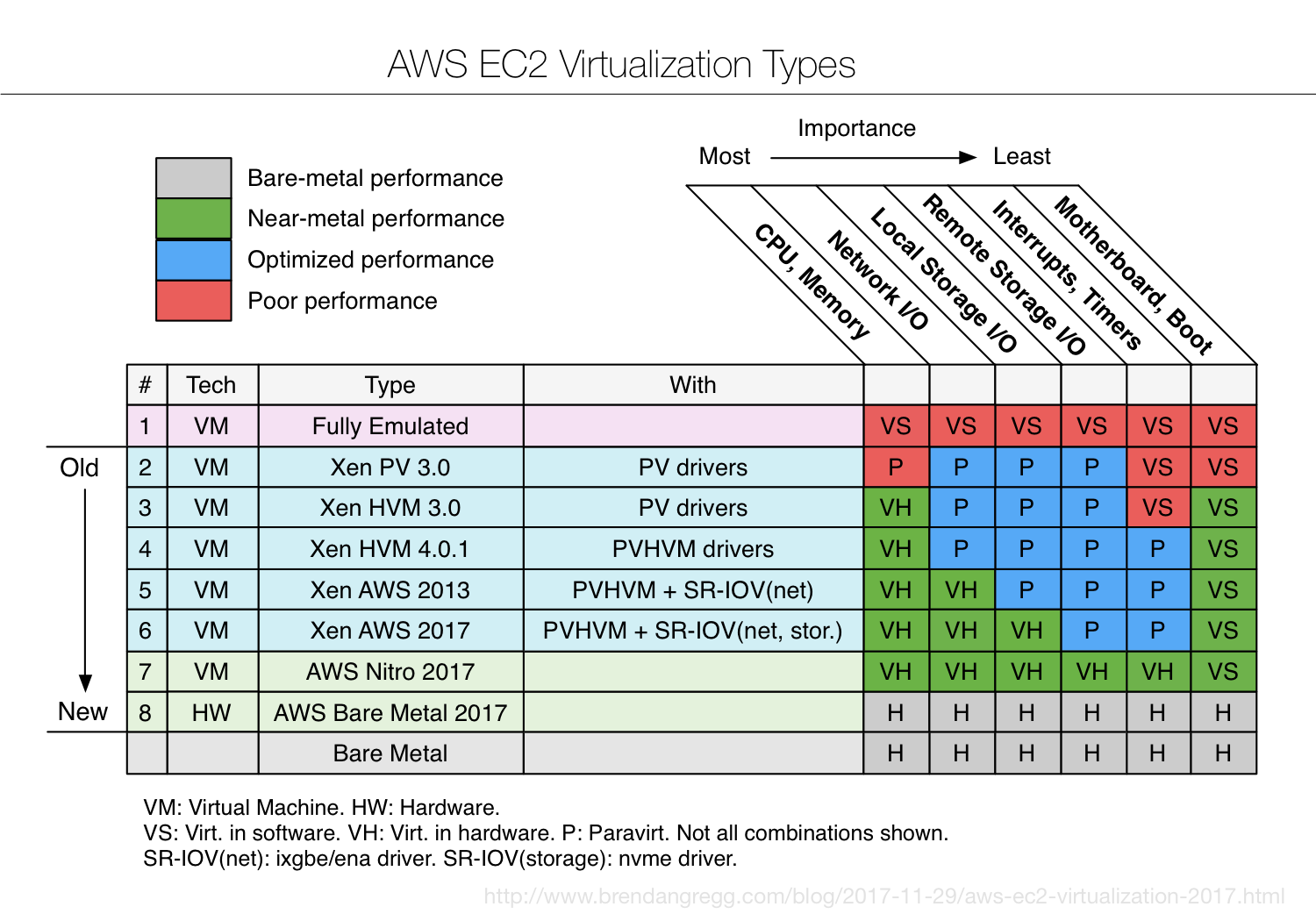
A very good summary of the advancement of virtualization technologies used in AWS EC2. The newest instance type offered is simply AWS Bare Metal, which provides all the hardware access with little performance overhead, while still retaining the benefits of cloud – elasticity etc.
AWS EC2 Virtualization 2017: explaining the different virtualization types, from emulation and binary substitution, paravirtualization and Xen, PV, HVM, and PVHVM modes, and the new Nitro hypervisor